To configure Microsoft 365/Office365 in Logpoint, you must first configure it in the Azure portal and retrieve the Client secret, Certificate Thumbprint, Certificate File, tenant ID, client ID and Subscription ID.
Note
While we provide Azure portal instructions in this guide, it’s important to be aware that the Azure portal interface may change over time. To ensure you have the most up-to-date information and to navigate any potential changes in the Azure portal interface, we recommend referring to the official Azure portal documentation.
Go to the Azure Portal.
Go to Microsoft Entra ID >> App registrations.
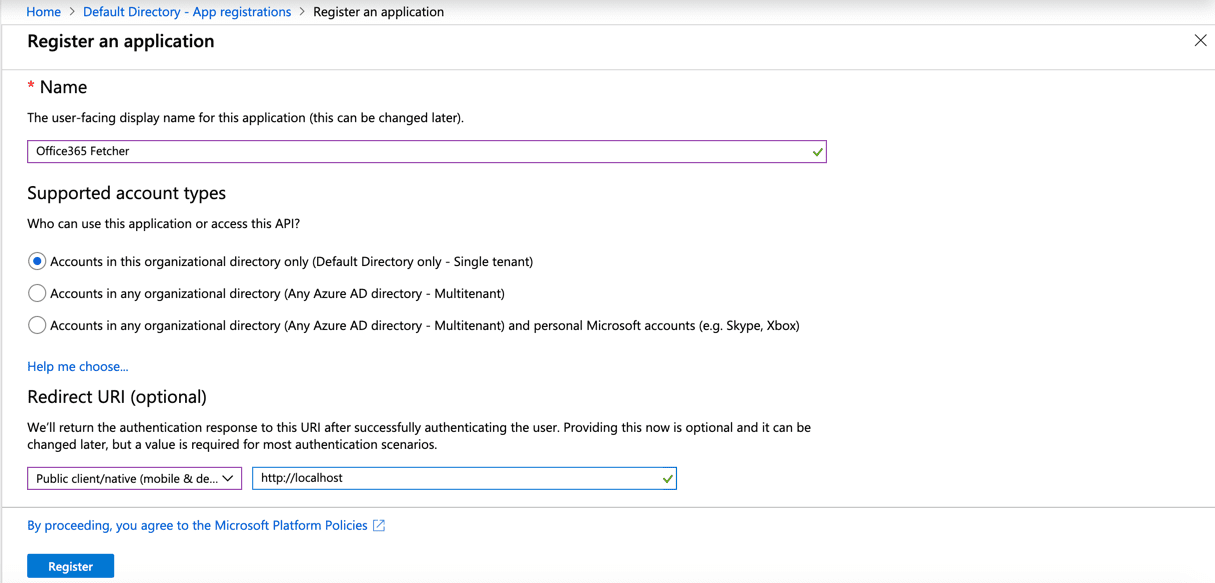
Click New registration.
Enter a Name.
Select Supported account types.
In the Redirect URI (optional):
7.1 Select Public client (mobile & desktop).
7.2 Enter the following address.
http://localhost
Click Register.
Creating a New Application¶
Note
You need the Application (client) ID and the Directory (tenant) ID to Configure the Office365 Fetcher in Logpoint and to Configure Office365 from Log Source.
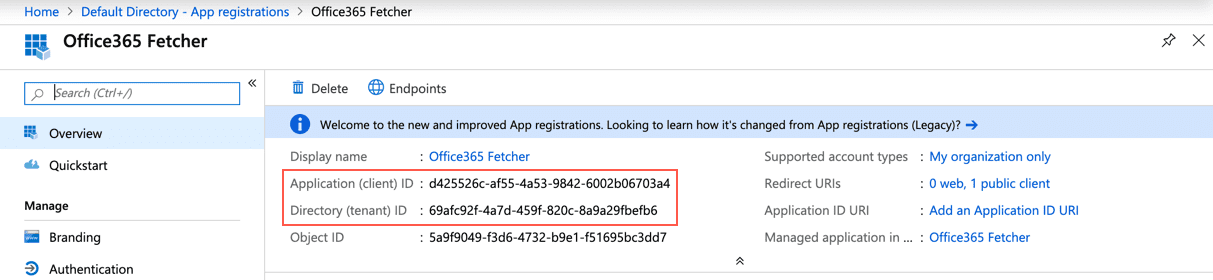
Application ID¶
Go to API permissions and click Add a permission.
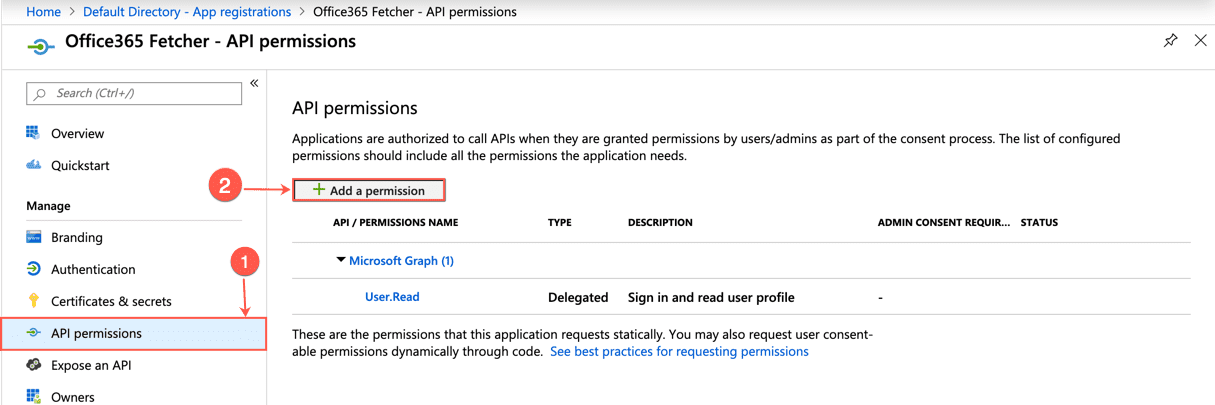
Adding a Permission¶
Click Microsoft APIs.
Select Office 365 Management APIs.
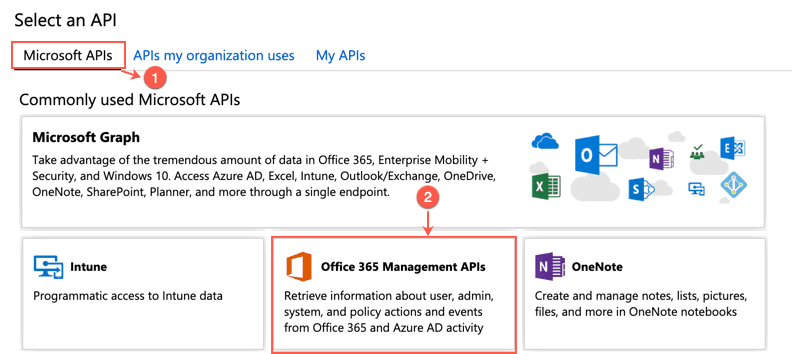
Selecting Office 365 Management APIs¶
Click Application permissions.
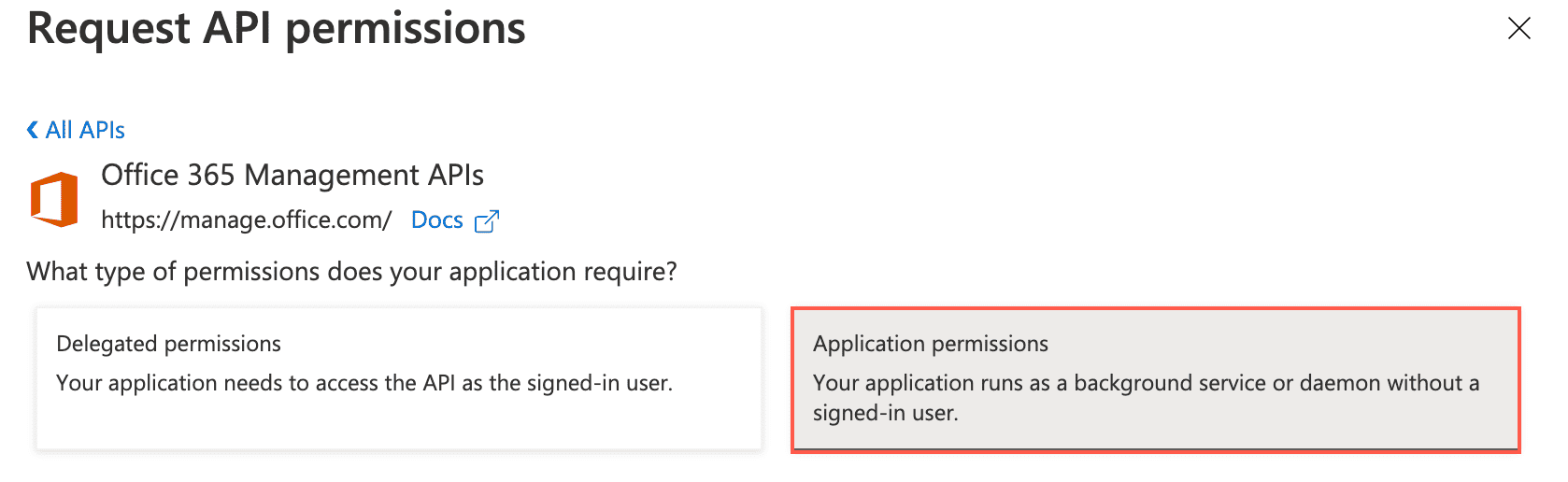
Application Permissions¶
Select all the available read permissions.
Click Add permissions.
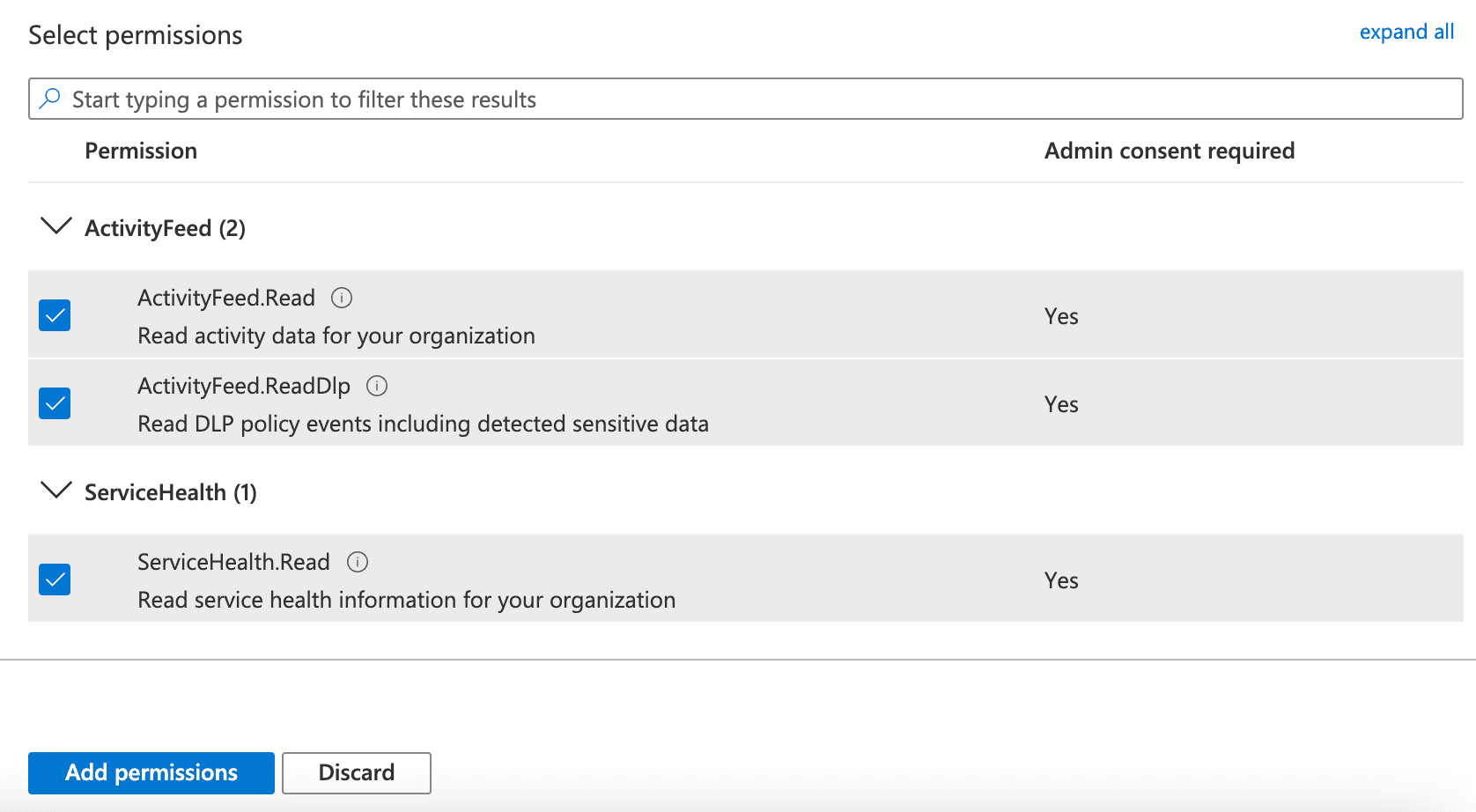
Selecting Read Permissions¶
Click Grant admin consent for Default Directory.
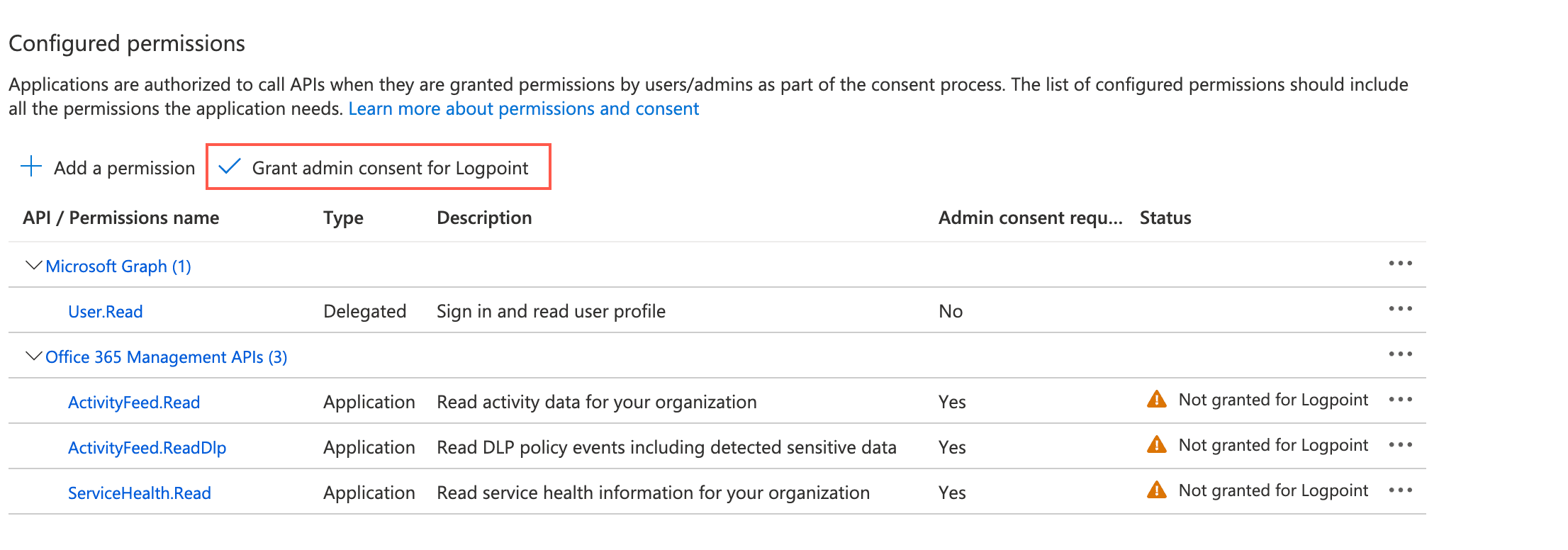
Granting Admin Consent¶
Click Yes.
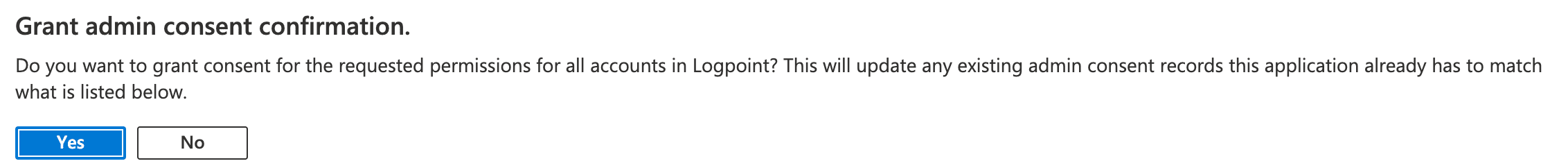
Confirmation Dialog Box¶
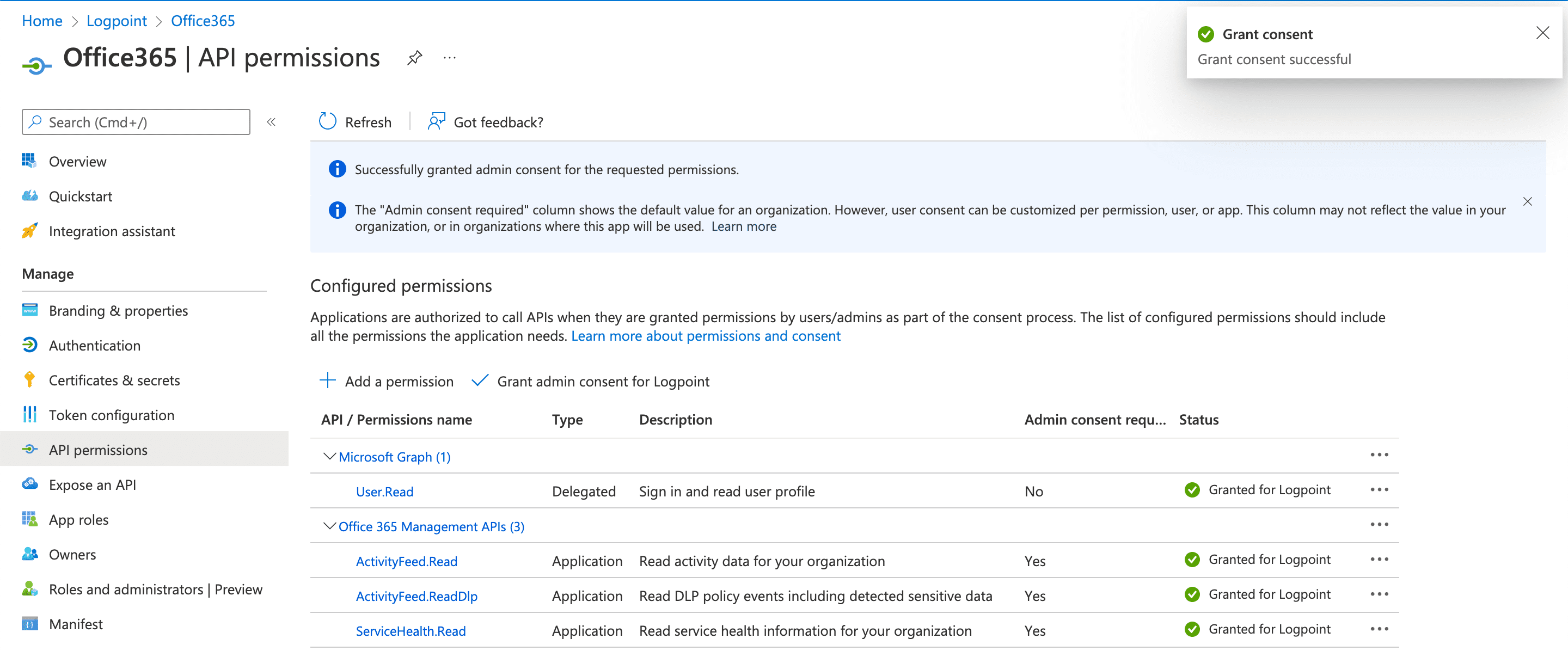
Grant Consent¶
Go to Authentication.
Enable Allow public client flows to Yes.
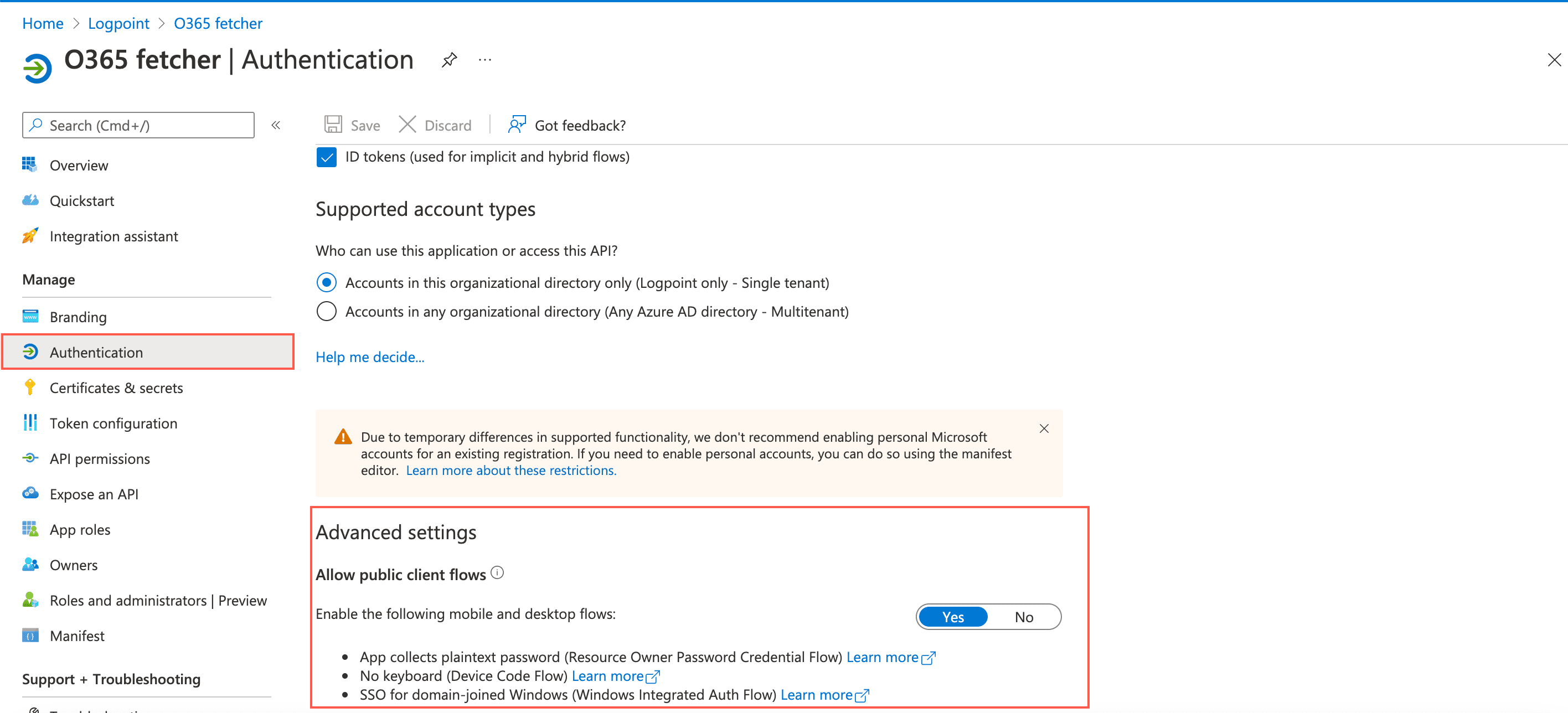
Public Client Flows¶
Alternatively, you can add the following key to the Manifest in the Azure portal.
"allowPublicClient": true
Click Certifictes & secrets and Client secrets.
Click New client secret.

Client Secret¶
Enter a Description.
Select expiration date for the client secret in the Expires.
Click Add.

Adding a Client Secret¶
Run the following commands to generate certificates. The certificates can be generated from any device (Linux server/Windows machine) where OpenSSL is installed. We recommend using Logpoint console via li-admin as OpenSSL is pre-installed in Logpoint.
1.1. Enter the following command in command prompt to generate a certificate key:
openssl genrsa -out server.pem 20481.2. Enter the following command to create a certificate request:
openssl req -new -key server.pem -out server.csr1.3. Enter the following command in the command prompt to generate certificates:
openssl x509 -req -days 365 -in server.csr -signkey server.pem -out server.crt
Save the two generated certificates. You will upload the certificate with the .crt extension to the Azure Portal and use the .pem extension certificate when configuring Office365 in Logpoint.
Click Certificates & secrets on application page in Microsoft Entra ID.
Click Certificates and Upload Certificate.
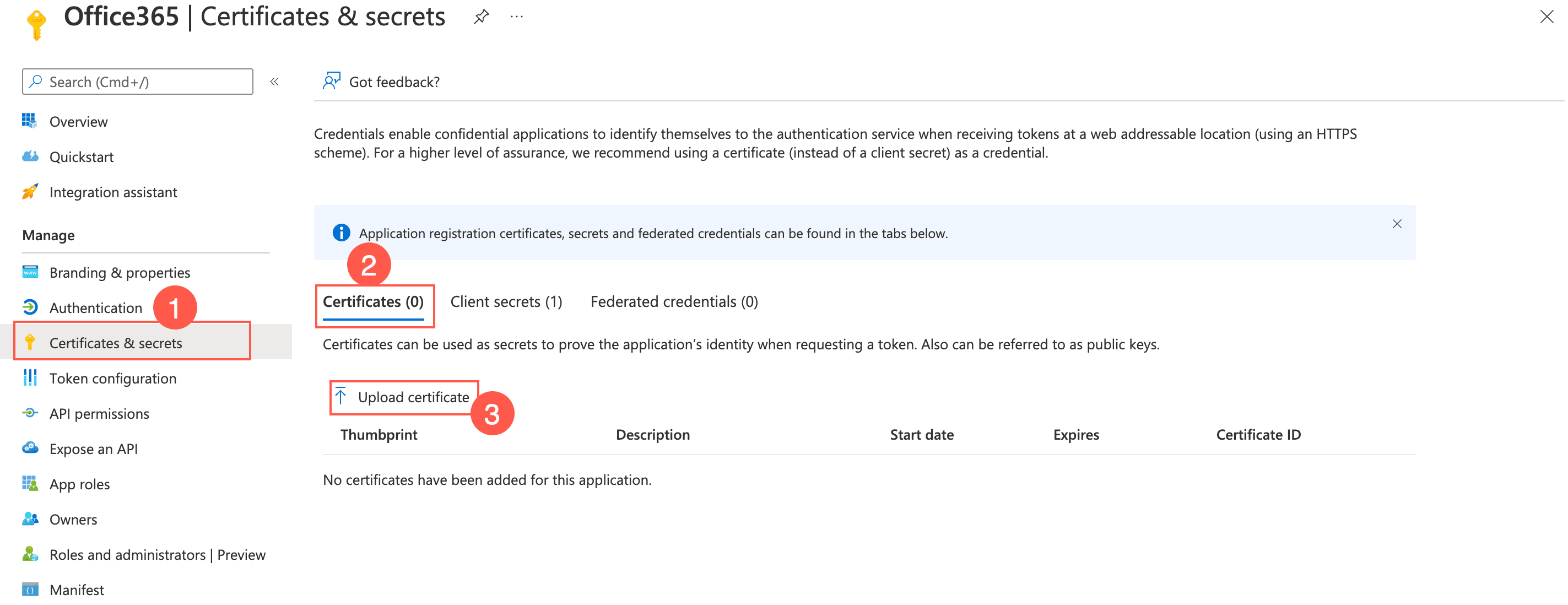
Uploading a Certificate¶
Select and upload the previously saved certificate with the extension .crt.
Enter a Description for the certificate.
Click Add.
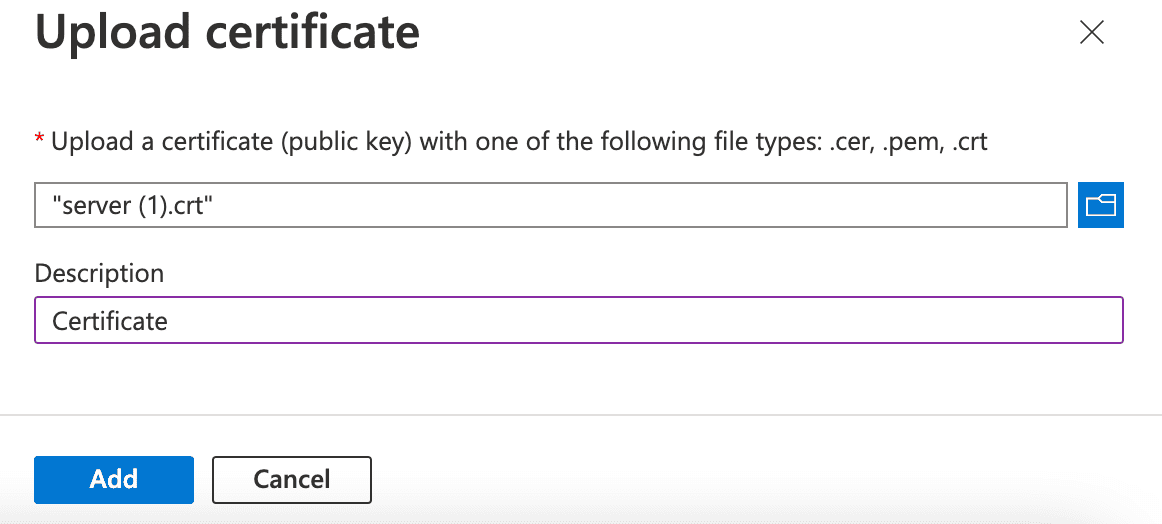
Uploading a Certificate¶
Note down the Thumbprint of the certificate. You need it to Configure the Office365 Fetcher in Logpoint.
Value of Client Secret¶
After configuring Office365 in Azure Portal and retrieving authentication credentials, you can now setup Office365 in Logpoint.
When you configure and run Office365 for the first time, a subscription is created to different audit log sources in the API. Once set, there is a time gap of 12 to 24 hours before the logs start to come in.
Add a normalization policy using the Office365CompiledNormalizer, which normalizes and standardizes logs for storage, analysis, and retrieval. This normalization policy can be used in the processing policy to process Office365 logs.
Go to Settings >> Configuration from the navigation bar and click Normalization Policies.
Click Add.
Enter a Policy Name.
Select Office365CompiledNormalizer.
Click Submit.
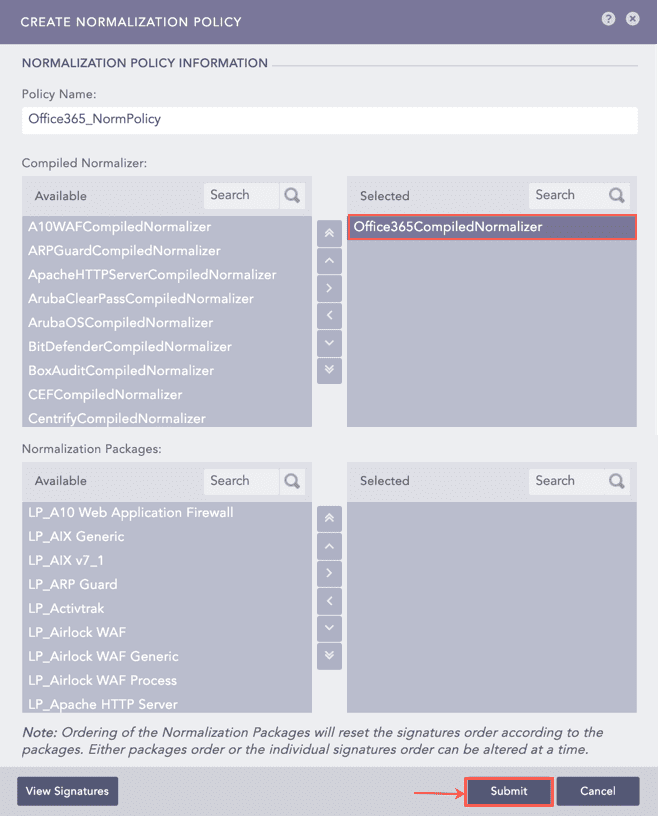
Adding a Normalization Policy¶
Go to Settings >> Configuration from the navigation bar and click Processing Policies.
Click Add.
Enter a Policy Name.
Select the Normalization Policy created for Office365.
Select the Enrichment Policy and Routing Policy.
Click Submit.
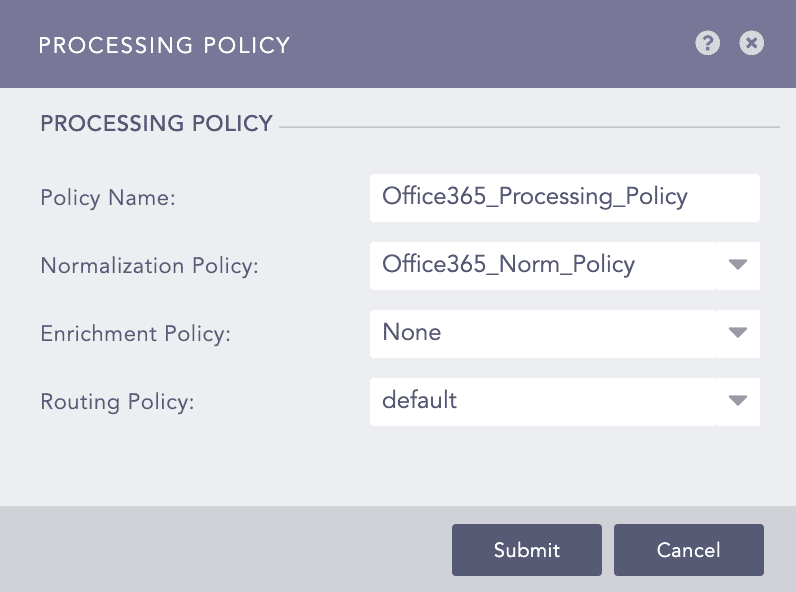
Adding a Processing Policy¶
After adding normalization and processing policies, you can now add Office365 Fetcher in Logpoint. Before that, you must also configure Microsoft Entra ID and retrieve the office365 authentication credentials.
Go to Settings >> Configuration from the navigation bar and click Devices.
Click the Add collectors/fetchers ( ) icon under Actions of the localhost device.
) icon under Actions of the localhost device.
Click Office365 Fetcher.
Click Add.
Select a mode of Authentication.
If you select Public Client,
Enter the identifier of your Microsoft 365 Tenant ID in Subscription ID.
Enter the Office365 Username and Password.

Public Client¶
If you select Client Secret,
Enter the identifier of your Microsoft 365 Tenant ID in Subscription ID.
Enter the value of client secret in the Client Secret.

Client Secret¶
If you select Certificate,
Enter the identifier of your Microsoft 365 Tenant ID in Subscription ID.
Enter the Office365 Certificate Thumbprint in the Certificate Thumbprint.
Upload the previously saved Certificate with the .pem extension in the Certificate File.
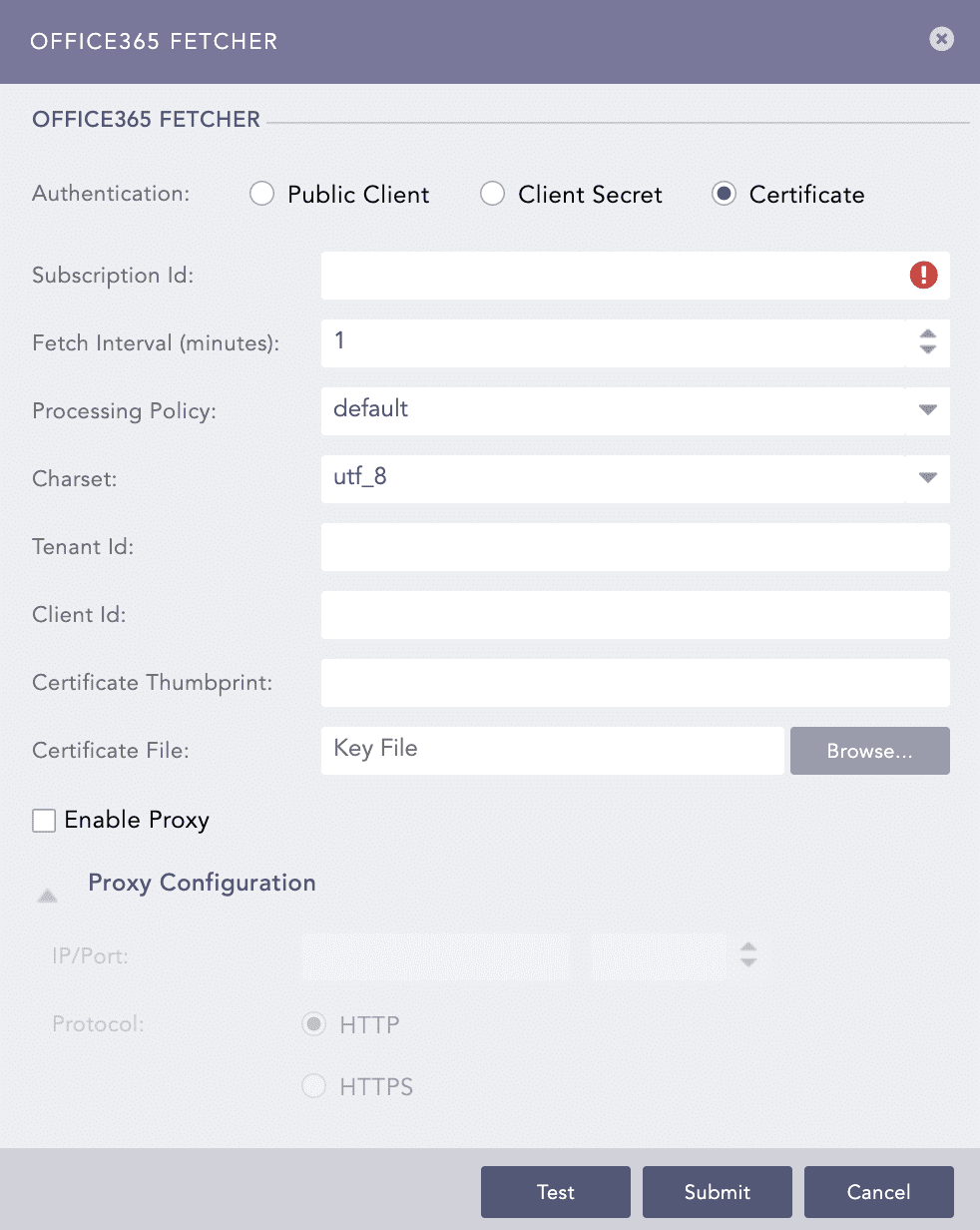
Certificate Thumbnail¶
Enter the Fetch Interval (minutes).
Select a Processing Policy that uses the previously created normalization policy.
Enter the Directory (tenant) ID in the Tenant ID.
Enter the Application (client) ID in the Application ID.
Select Enable Proxy if you use a proxy server.
In Proxy Configuration:
12.1 Enter the proxy server IP Address and the Port number.
12.2 Select HTTP or HTTPS protocol.
Click Test to validate the configuration.
Click Submit.
Office365 consists of the log source template Microsoft365 which has pre-defined settings and configurations to fetch logs. However, there are some fields in the template which must be configured manually.
Go to Settings >> Log Sources from the navigation bar and click + Add Log Source.
Click + Create New and select Microsoft365.
In source, add details about the log source from where the S3Fetcher fetches logs.
Click Source.
Enter the Log Source’s Name.
Select the frequency at which data is retrieved in Fetch Interval (min).
Select the Charset and Time Zone.
Connector is a pathway for transmitting logs from various sources to Logpoint. In connector, configure how S3Fetcher and the log source communicate with each other.
Click Connector.
Enter the Client Secret, Subscription Id, Tenant ID, and Client ID. You get all of these values while Configuring Office365 Fetcher in Microsoft Entra ID.
In routing, create repos and routing criteria for S3 Fetcher. Repos are locations where incoming logs are stored and routing criteria is created to determine the conditions under which these logs are sent to repos.
To create a repo:
Click Routing and + Create Repo.
Enter a Repo name.
In Path, enter the location to store incoming logs.
In Retention (Days), enter the number of days logs are kept in a repository before they are automatically deleted.
In Availability, select the Remote logpoint and Retention (Days).
Click Create Repo.
In Repo, select the created repo to store logs.
To create Routing Criteria:
Click + Add row.
Enter a Key and Value. The routing criteria is only applied to those logs which have this key-value pair.
Select an Operation for logs that have this key-value pair.
3.1. Select Store raw message to store both the incoming and the normalized logs in the selected repo.
3.2. Select Discard raw message to discard the incoming logs and store the normalized ones.
3.3. Select Discard entire event to discard both the incoming and the normalized logs.
In Repository, select a repo to store logs.
Click the ( ) icon under Action to delete the created routing criteria.
) icon under Action to delete the created routing criteria.
In normalization, select normalizers for the incoming logs. Normalizers transform incoming logs into a standardized format for consistent and efficient analysis.
Click Normalization.
You can either select a previously created normalization policy from the Select Normalization Policy dropdown or select a Normalizer from the list and click the swap icon.
In enrichment, select an enrichment policy for the incoming logs. Enrichment policies are used to add additional information to a log, such as user information, device type or geolocation, before analyzing it. For more information on enrichment, go to: Enrichment Policies.
Click Enrichment.
Select an Enrichment Policy.
Click Create Log Source to save the configurations of Source, Connector, Routing, Normalization, and Enrichment.
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support